更新可疑模块检测
This commit is contained in:
@@ -232,7 +232,7 @@ void ThreadStackWalk() {
|
||||
CloseHandle(hThreadSnap);
|
||||
}
|
||||
}
|
||||
void WalkProcessMoudle(DWORD pID,HANDLE pHandle,WCHAR* pMoudleName) {
|
||||
void WalkProcessMoudle(DWORD pID,HANDLE pHandle,WCHAR* pMoudleName,BOOL pCheckMoudle) {
|
||||
|
||||
MODULEENTRY32 moduleEntry;
|
||||
HANDLE handle = NULL;
|
||||
@@ -246,6 +246,13 @@ void WalkProcessMoudle(DWORD pID,HANDLE pHandle,WCHAR* pMoudleName) {
|
||||
return;
|
||||
}
|
||||
do {
|
||||
if (pCheckMoudle) {
|
||||
CdigitalSig DigitalSig(moduleEntry.szExePath);
|
||||
DWORD dDigitalState = DigitalSig.GetDigitalState();
|
||||
if (dDigitalState != DIGITAL_SIGSTATE_VALID) {
|
||||
printf("\t => [ģ<><C4A3>ɨ<EFBFBD><C9A8>] <20><><EFBFBD><EFBFBD><E2B5BD><EFBFBD><EFBFBD>ģ<EFBFBD><C4A3>(Ҳ<><D2B2><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>) ·<><C2B7> %ws <20><><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD> %ws pid %d \n", moduleEntry.szExePath, pMoudleName, pID);
|
||||
}
|
||||
}
|
||||
DWORD64 ReadNum = 0;
|
||||
if (ReadProcessMemory(pHandle, moduleEntry.modBaseAddr, AllocBuff, 0x200, &ReadNum)) {
|
||||
if (AllocBuff[0] == 'M' && AllocBuff[1] == 'Z') {
|
||||
@@ -286,7 +293,6 @@ void ProcessStackWalk() {
|
||||
//<2F><>ӡ<EFBFBD><D3A1><EFBFBD><EFBFBD><EFBFBD><EFBFBD><EFBFBD>ͽ<EFBFBD><CDBD><EFBFBD>ID
|
||||
HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS, false, pe32.th32ProcessID);
|
||||
if (hProcess) {
|
||||
WalkProcessMoudle(pe32.th32ProcessID, hProcess, pe32.szExeFile);
|
||||
WCHAR szImagePath[MAX_PATH];
|
||||
WCHAR pszFullPath[MAX_PATH];
|
||||
if (GetProcessImageFileName(hProcess, szImagePath, MAX_PATH))
|
||||
@@ -298,6 +304,8 @@ void ProcessStackWalk() {
|
||||
if (dDigitalState == DIGITAL_SIGSTATE_REVOKED || dDigitalState == DIGITAL_SIGSTATE_EXPIRE) {
|
||||
printf("\t => [<5B><><EFBFBD><EFBFBD>ɨ<EFBFBD><C9A8>] <20><><EFBFBD><EFBFBD><E2B5BD><EFBFBD><EFBFBD>ǩ<EFBFBD><C7A9><EFBFBD><EFBFBD><EFBFBD><EFBFBD> ·<><C2B7> %ws static %d \n", pszFullPath, dDigitalState);
|
||||
}
|
||||
WalkProcessMoudle(pe32.th32ProcessID, hProcess, pe32.szExeFile, dDigitalState == DIGITAL_SIGSTATE_VALID);
|
||||
|
||||
}
|
||||
}
|
||||
CloseHandle(hProcess);
|
||||
|
||||
@@ -1,5 +1,6 @@
|
||||
# DuckMemoryScan
|
||||
一个简单寻找无文件落地后门的工具,由huoji花了1天编写,编写时间2021-02-24
|
||||
!!!本程序需要64位编译才能回溯x64的程序堆栈,请勿执行32位编译!!!
|
||||
|
||||
# 运行截图
|
||||
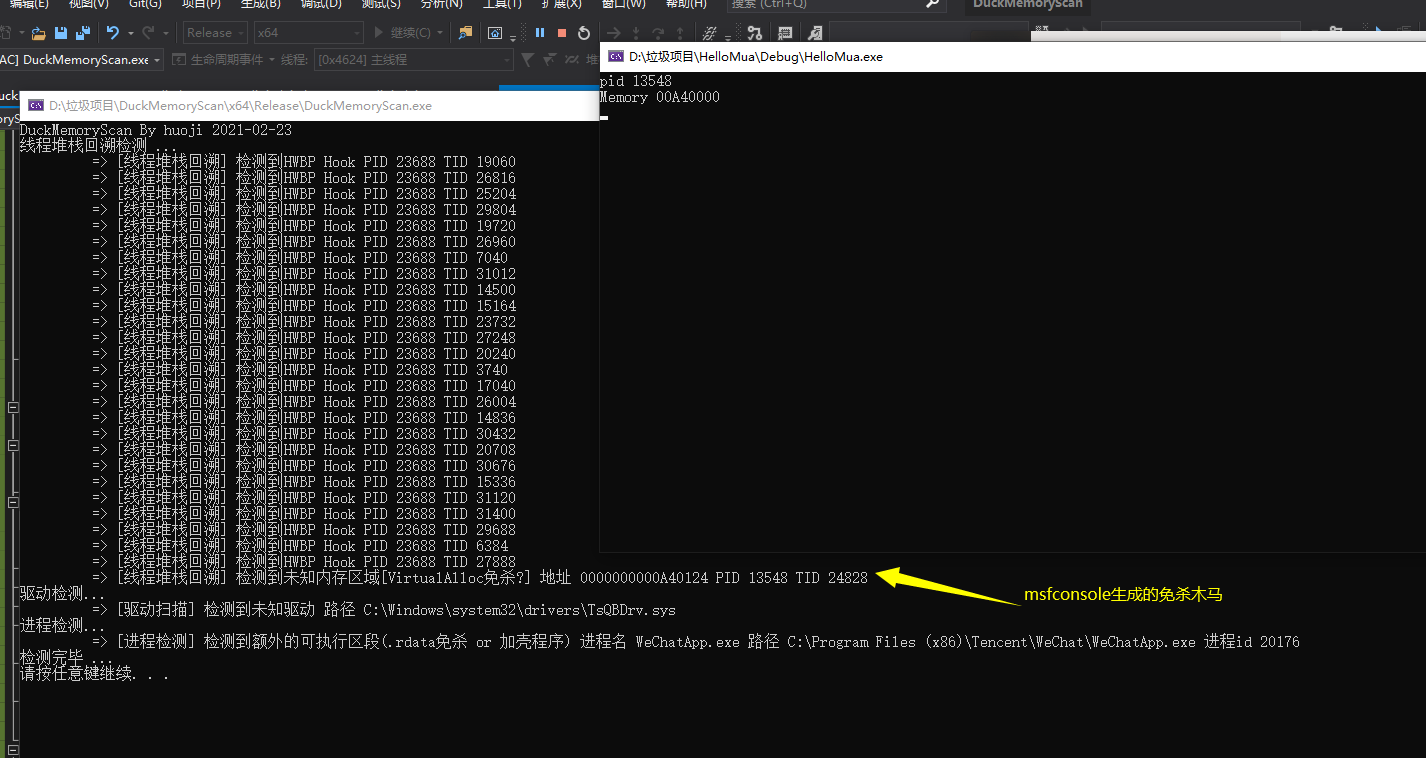
|
||||
@@ -10,7 +11,7 @@
|
||||
3. 可疑进程检测(主要针对有逃避性质的进程[如过期签名与多各可执行区段])
|
||||
4. 无文件落地木马检测(检测所有已知内存加载木马)
|
||||
5. 简易rootkit检测(检测证书过期/拦截读取/证书无效的驱动)
|
||||
|
||||
6. 检测异常模块,检测绝大部分如"iis劫持"的后门(2021年2月26日新增)
|
||||
# 免杀木马检测原理:
|
||||
所有所谓的内存免杀后门大部分基于"VirtualAlloc"函数申请内存 之后通过各种莫名其妙的xor甚至是aes加密去混淆shellcode达到"免杀"效果.
|
||||
本工具通过线程堆栈回溯方法(StackWalkEx函数)遍历线程,寻找系统中在VirtualAlloc区域执行代码的区域,从而揪出"免杀木马"
|
||||
@@ -23,6 +24,9 @@
|
||||
2. 线程指向一个NOIMAGE内存
|
||||
本工具将会通过第一种特征检测出所有"无文件落地木马"
|
||||
|
||||
# 异常模块检测原理
|
||||
本工具将会扫描所有带签名程序的模块列表并且检测其中模块是否存在签名,如果不存在则发出提示.本检测存在较多误报,但将会检测到类似IIS劫持的特殊模块
|
||||
|
||||
# 使用方式
|
||||
编译 运行 得到信息列表
|
||||
|
||||
|
||||
Reference in New Issue
Block a user