d6caf059402fac86dda483a0f9aae1d18669f8db
- Ryujin is now fully capable of detecting debuggers from both userland and kernel land.
- Ryujin inserts its detection stub without breaking application logic.
- Ryujin supports two modes:
- Troll – triggers a BSOD using a Microsoft Windows bug.
- Normal – simply calls NtTerminateProcess when a debugger is detected.
- This implementation can be improved in the future to handle more advanced detection methods, but it's good for now.
Ryūjin Protector
Ryūjin Protector is an open-source Bin2Bin obfuscation, protection, and DRM tool for Windows PE binaries targeting the Intel x64 architecture(Only).
Features
- Junk Code Insertion + Code Mutation (Fully randomic without breaking the original logic)
- IAT Call Access Obfuscation(With obfuscated handlers access)
- Random Section naming(Default name: Ryujin)
- Mathematical Operators Virtualization(aka: Ryūjin MiniVM)
- Obfuscated code Encryption(Using TeaDelKew Algorithm)
- Anti-Debug User + Kernel(Planned)
- Anti-Dump(Planned)
- Anti-Disassembly(Planned)
- Troll Reversers(Exclusive Planned)
Goals
Ryūjin was designed and developed for the study of obfuscators with Bin2Bin capabilities, making it a viable project for use by third parties as well as serious information security students. This includes: Commercial Developers, Indie Developers/Cheat Developers, Anti-Cheat Developers, Malware Developers, Malware Analysts, and Security Researchers.
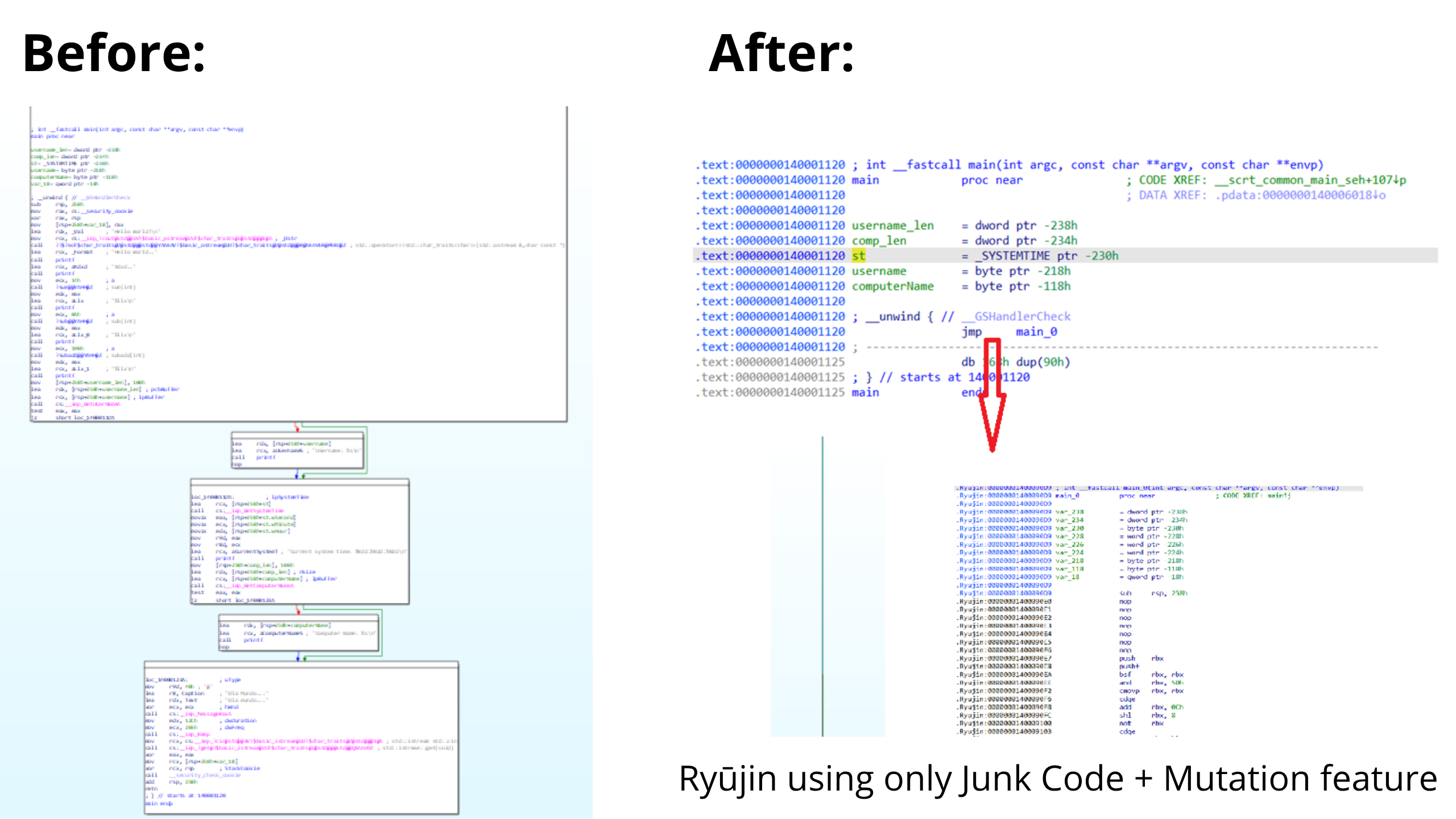
A Simple Comparison on a "main" function. before and after applying Ryūjin:
This is only a small demo with only one Ryūjin feature, others feature together produce a better result.
Getting Started
GITHUB_WIKI_URL
Languages
C++
99.9%